By Talal Haj Bakry and Tommy Mysk
If you enjoyed this work, you can support us by checking out our apps:
- TextCrafter – Craft & Share
- Ctrl – The best presentation companion for your Apple Watch
- Canvas – Draw Together, Wirelessly!
tl;dr
With Tesla’s current design, if an attacker has the email and password of a victim’s Tesla account, they can drive away with the victim’s Tesla, even if two-factor authentication is enabled. Tesla Product Security team has investigated this issue and determined that this is the intended behavior.
Video
Introduction
Phishing and social engineering attacks are not uncommon. However, an attacker who gets a hold of leaked or stolen credentials shouldn’t have it all. This post shows that Tesla doesn’t protect its users, or vehicles, against stolen credentials. Unfortunately, an attacker who somehow gets the credentials of a vehicle’s Tesla account can take control of the car and drive away with it.
The major problem with the design is that Tesla only requires the email and password of a Tesla account as well as being physically near the Tesla vehicle to activate a phone key. With an activated phone key a user, or an attacker, has full control of the vehicle. The flow doesn’t require the user to be inside the car or to use another physical factor for authentication, such as a Tesla key card or scanning a QR code that the Tesla’s touchscreen displays.
Attack Concept
We developed a hypothetical, but not far-fetch, scenario based phishing and social engineering to obtain the credentials of a Tesla account. We used a captive Wi-Fi network whose SSID looks familiar to Tesla owners. We named the Wi-Fi network “Tesla Guest” to match the guest network Tesla offers at its service centers. The Wi-Fi network displays a captive portal that is shown right after joining the network. On the captive portal, we showed a fake sign-in screen that matches the real sign-in screen on Tesla’s website.

Now, all the attacker needs to do to target a victim is to broadcast this Wi-Fi network in a place that Tesla drivers frequently visit; a Tesla Supercharger. What better place to find Tesla drivers other than a Tesla Supercharger!
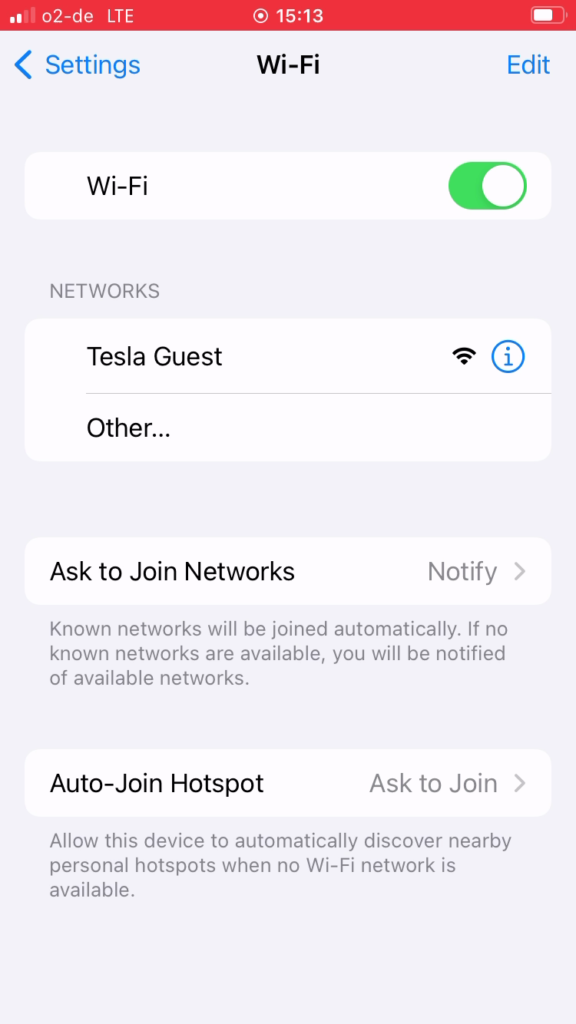
Attack Preparation
Theoretically, a Tesla driver at a Tesla Supercharger would discover this Wi-Fi network and attempt to join it as it looks as if it was offered by Tesla. When joining the Wi-Fi network, the captive portal will be shown on the driver’s smartphone prompting the driver to sign in. Since this captive portal is fully controlled by the attacker, everything typed on this portal is logged and shown to the attacker in real-time. The fake sign-in screen mimics the real Tesla sign-in screen and prompts for the Tesla account email, password, and two-factor one-time passcode (OTP). As a result, the victim would enter the account details as if they were signing in on a Tesla official website, or app.
The attacker hopes that the victim would enter the correct details in order to join what seems to be a Tesla free Wi-Fi network only offered to Tesla drivers, at a Tesla Supercharger. Everything sounds legit.
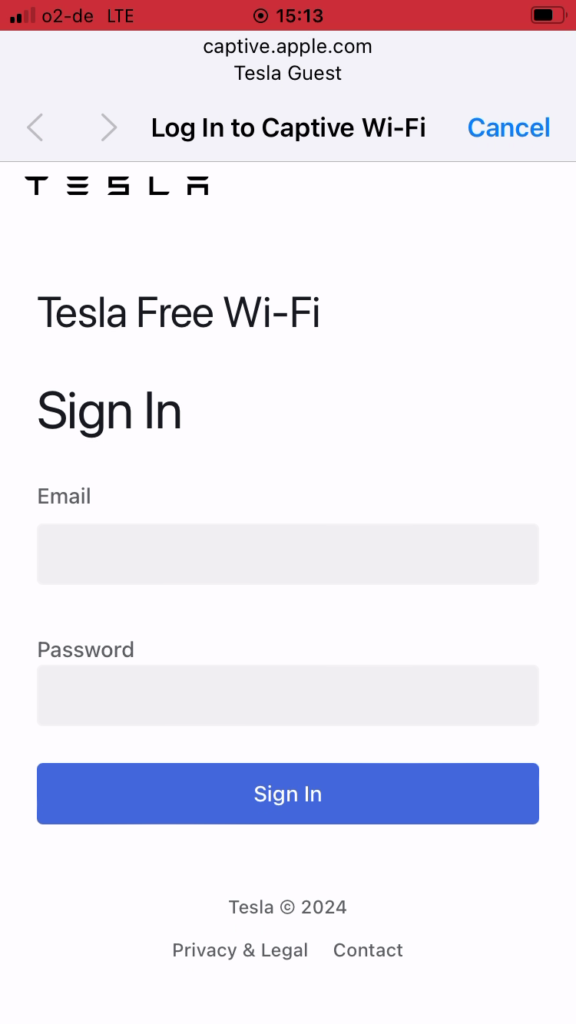
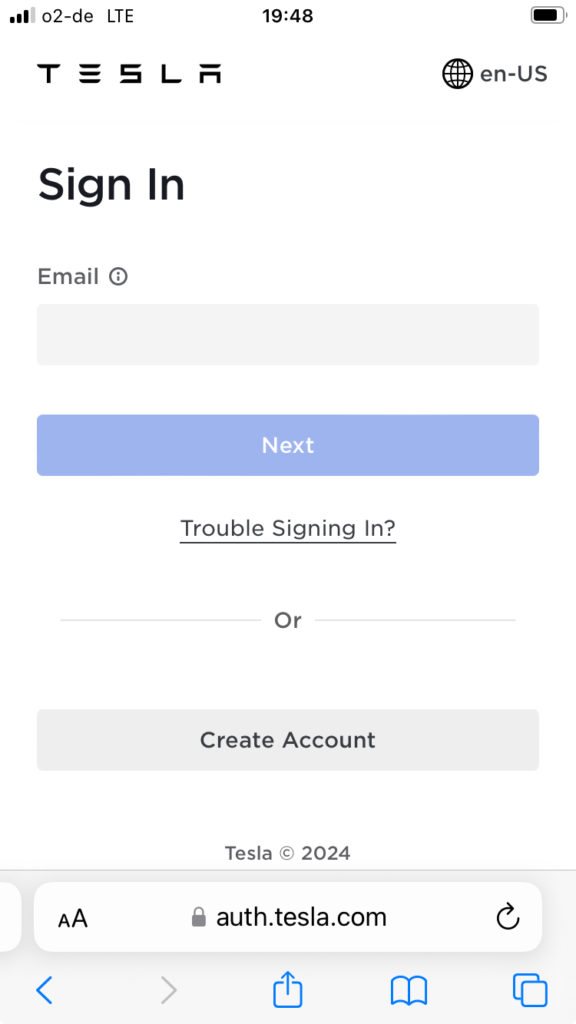
For the purpose of recording this demo to illustrate this attack, we used a Flipper Zero to run the captive Wi-Fi network. We cannot stress enough that many devices are capable of doing the same. In fact, a laptop would fit this scenario the best as the attacker needs to react within 30 seconds, in case the victim’s account is protected by two-factor authentication.
As the attacker receives the Tesla account information in real-time, the attacker enters these details in the official Tesla mobile app. If the victim’s account is not protected by two-factor authentication, the attacker will successfully sign in. If the account is protected by two-factor authentication, the fake captive portal will prompt the victim to enter the one-time passcode, which is relayed in real-time to the attacker. Then, the attacker enters the OTP in the official app and successfully signs in.
At this point, the victim does not receive any push or email notification that a new sign-in to the Tesla account has been made. The session in the Tesla app already starts showing live information about the vehicle, such as precise location and state.
The Attacker is in Control
The attacker now possesses a valid session in the mobile app that allows for tracking the vehicle. However, the attacker cannot control the vehicle yet. For that, the phone key has to be activated. It turns out, this is the simplest step in the entire process. At any time, the attacker can just turn the bluetooth and location services on their smartphone, push the “Set up” button on the app, walk by the vehicle, and the phone key will be activated. And from this moment on, the attacker is in full control.
Since the attacker receives live tracking information about the vehicle, it would be too blatant to drive away with the car now at the Supercharger. The owner is still nearby. Ideally, the attacker would track the vehicle and wait for the right moment when the vehicle is left unattended.
To make things worse, the Tesla website doesn’t provide information about how many active sessions a user has. The app doesn’t show this either. Moreover, in the event that the owner navigates to the list of locks shown by the Tesla’s touchscreen and sees a strange phone key, removing that unwanted phone key doesn’t terminate the session of the app associated with the key. Thus, the attacker can still receive live information about the vehicle and can re-activate the key at any moment.
Surprisingly, removing a phone key from the Tesla’s touchscreen requires authentication with a key card. And after successfully removing a phone key, the owner receives a push notification.
Tesla Product Security Responds
We are aware that that phishing and social engineering attacks are not covered by Tesla’s Bug Bounty program.
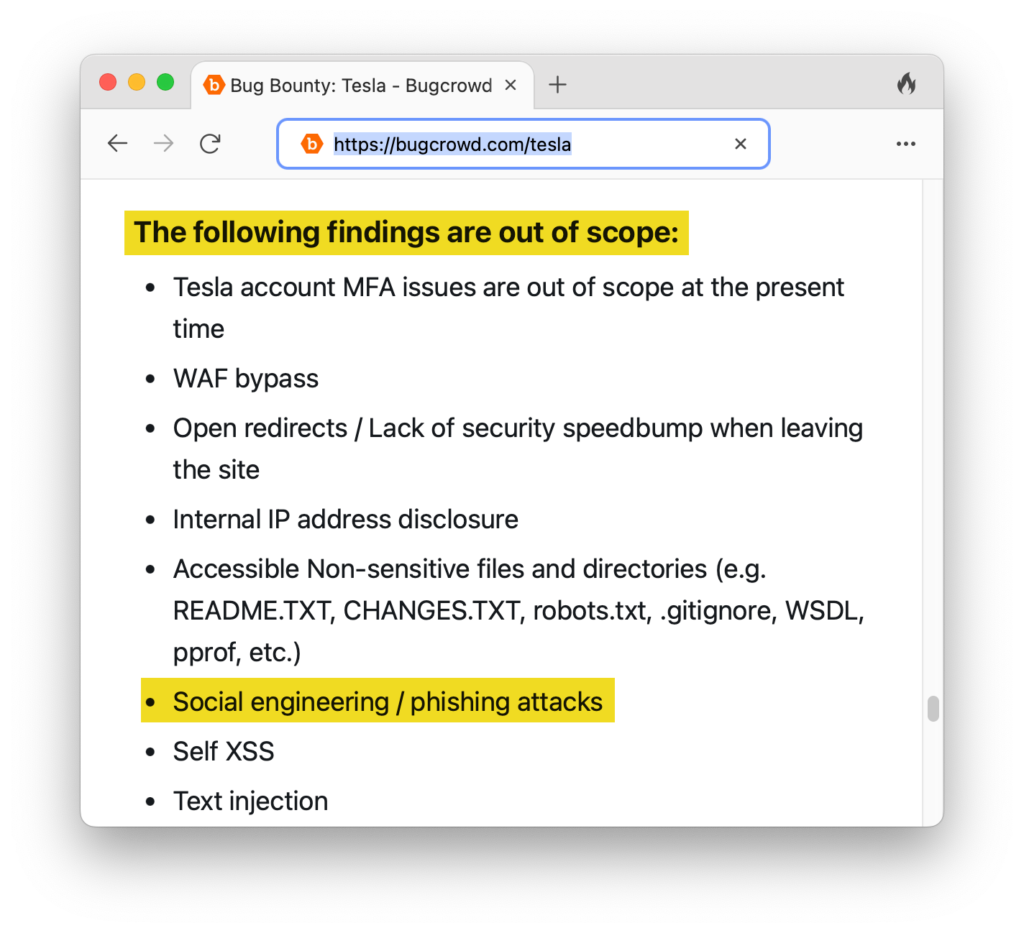
However, the Tesla owner’s manual clearly states that a phone key cannot be added without authenticating with a key card — the RFID cards or standard keys that come with a Tesla. As shown in the scenario, the attacker was able to add a phone key without having a key card. For us, this is a clear bug.
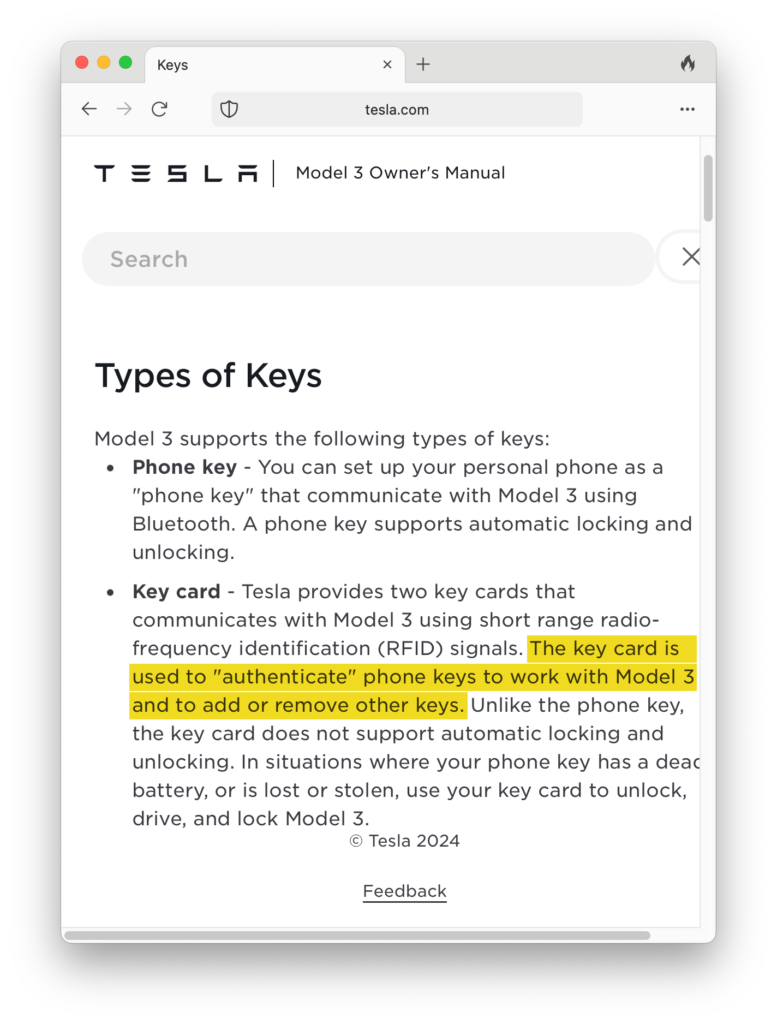
We reported it to Tesla Product Security and highlighted the link that states the relevant information.
The key card is used to “authenticate” phone keys to work with Model 3 and to add or remove other keys.
https://www.tesla.com/ownersmanual/model3/en_us/GUID-E004FAB7-1C71-448F-9492-CACF301304D2.html
Surprisingly, Tesla Product Security team determined that this is the intended behavior. In addition, they rejected that the card key is needed to authenticated a phone key, which is the opposite of what the owner’s manual says.
Hi Tommy,
Thanks for the report. We have investigated and determined that this is the intended behavior. The “Phone Key” section of the owner’s manual page you linked to makes no mention of a key card being required to add a phone key.
Thanks,
Tesla Product Security
Final Thoughts
We believe that this behavior is unsafe and Tesla vehicles clearly are vulnerable to phishing and social engineering attacks. We recommend the following remedies for this problem:
- Tesla should make key card authentication mandatory for adding new phone keys
- Tesla should notify owners when new keys are added
It’s worth mentioning that the “PIN to Drive” security feature that Tesla vehicles have wouldn’t prevent the attacker from driving the car. The phone key in the Tesla mobile app can bypass the “PIN to Drive.” Thus, the attacker can disable the PIN and drive away with the car.
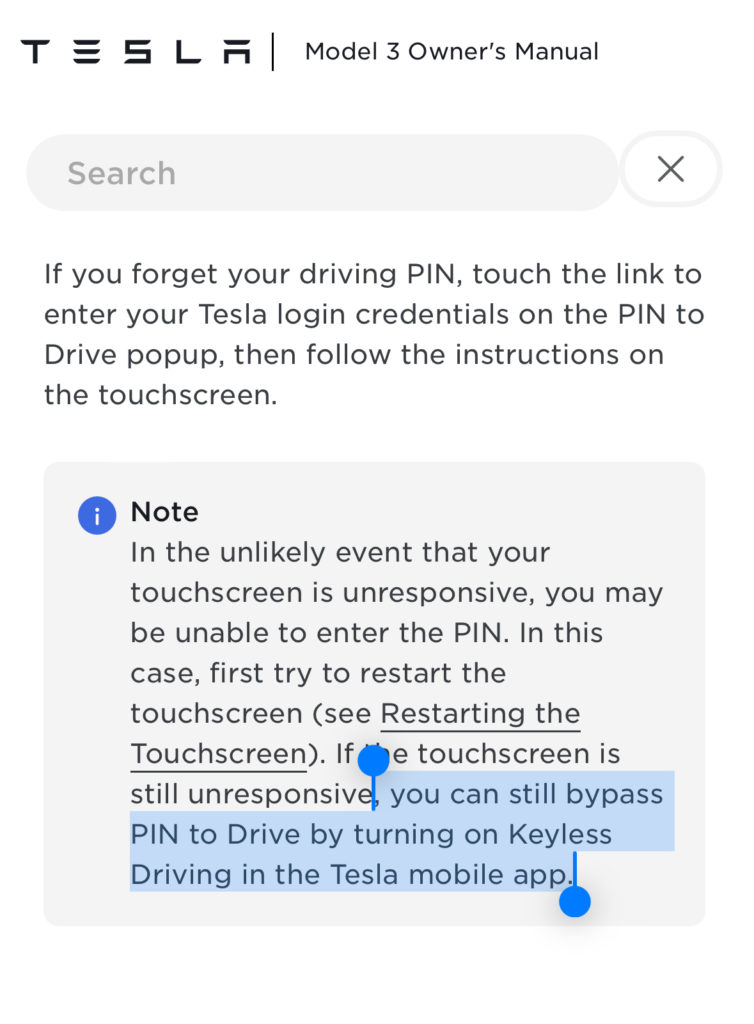
Phishing and social engineering attacks are very common today, especially with the rise of AI technologies, and responsible companies must factor in such risks in their threat models. If a victim was tricked to expose their credentials, they shouldn’t lose it all. They shouldn’t lose their car.
Hopefully, this post and video will raise awareness about this topic. If you have found this post helpful, share it with friends to spread the word, especially if they are Tesla owners.
Technical Information
- The test performed in Germany on March 3, 2024
- The issue reported to Tesla on March 4, 2024
- Tesla responded on March 6, 2024
- Tesla app version: 4.30.6, iOS
- Tesla software version: v11.1 2024.2.7