Popular iPhone and iPad Apps Snooping on the Pasteboard
Table of Contents
UPDATE (AUGUST 16, 2020): More apps crossed out *
UPDATE (JUNE 30, 2020): The list of apps in the original report from March 2020 is NOT an exhaustive list. We examined a sample of popular apps, and listed the ones that exhibited the behavior of excessive clipboard access. Many apps have been updated since then. In light of that, we tested the apps again. The apps that stopped reading the clipboard are crossed out.
Videos#
- Two apps; one snoops on the clipboard, the other doesn’t
- Exploit of the Universal Clipboard on Mac
- Method to view pasteboard events using Xcode
Introduction#
Apps on iOS and iPadOS have unrestricted access to the system-wide general pasteboard, also referred to as the clipboard. The potential security risks of this vulnerability have been thoroughly discussed in a previous article: Precise Location Information Leaking Through System Pasteboard. We have explored popular and top apps available on the App Store and observed their behaviour using the standard Apple development tools. The results show that many apps frequently access the pasteboard and read its content without user consent, albeit only text-based data.
The apps we chose in this investigation belong to various App Store categories, e.g. games, social networking, and news. As we described in our pervious article, the severity of the pasteboard vulnerability is greatest when popular and frequently-used apps exploit it. Thus, we targeted a variety of popular apps we found on the top lists of the App Store.
Methodology#
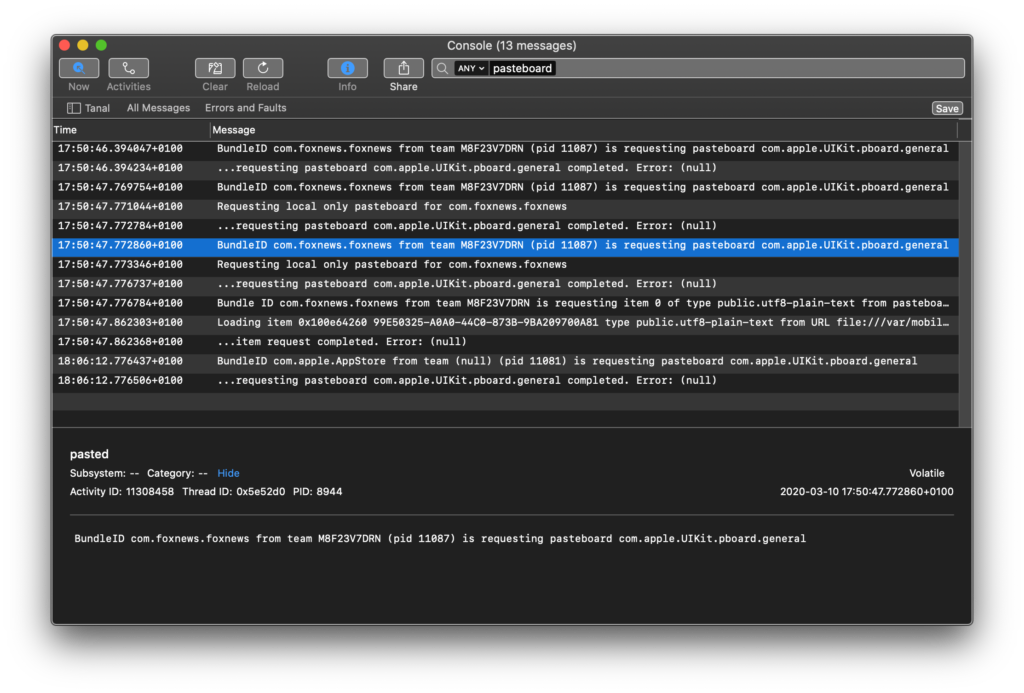
Apple provides Xcode and Xcode Command Line tools for developers to build apps for iOS, iPadOS, and macOS. We used these official tools to monitor and analyze the behavior of apps installed on our iOS and iPadOS devices. The method is simple: Once we connect and pair the devices with Xcode, we can read the system log of the device. Fortunately, all pasteboard events are clearly logged. Figure 1 shows an example of the system log output when the Fox News app is opened. The following explains the key information in the log output:
- The logs output all events, and is filtered by the keyword “pasteboard”
- The highlighted event in Figure 1 shows when the Fox News app requested access to the pasteboard with ID
com.apple.UIKit.pboard.general. This is the ID of the system-wide pasteboard - BundleID
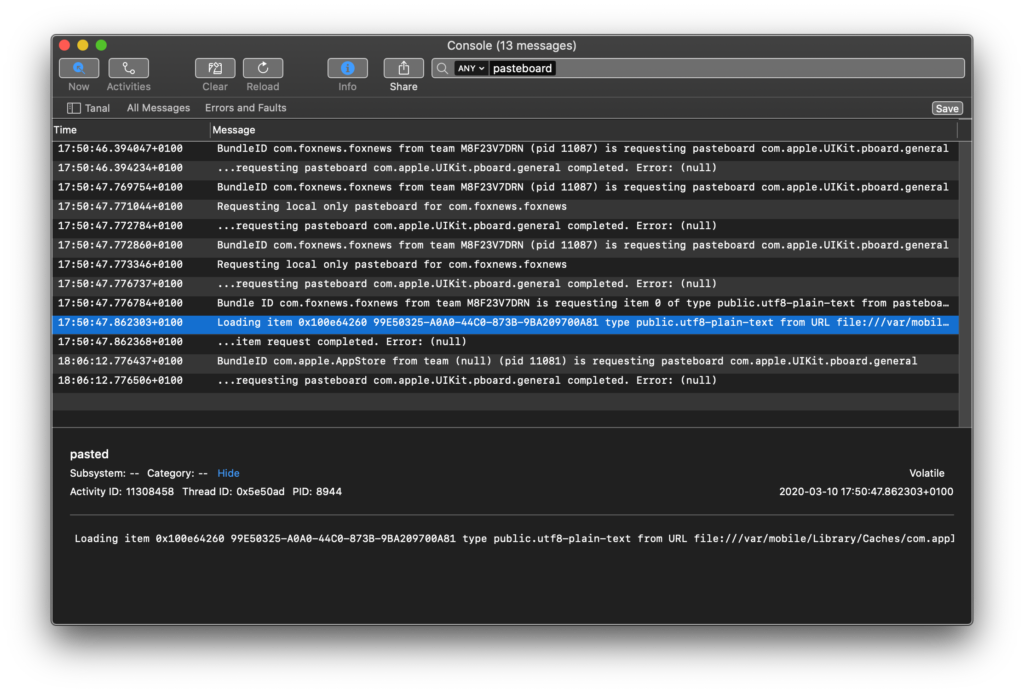
com.foxnews.foxnewsis the ID that uniquely identifies the Fox News app on the App Store - The event message that starts with “Loading item …” in Figure 2, indicates that the app has read the content of the pasteboard.
- The type
public.utf8-plain-textindicates that the content that the app has read is text.
This method can be performed by any iOS or Mac developer.
Criteria#
We include any app that requests and reads the content of the system-wide pasteboard every time it’s opened, and consider it to be highly suspicious. There are games and apps that do not provide any UI that deals with text, yet they read the text content of the pasteboard every time they’re opened.
Every app that is popular or on a top list according to the App Store rankings qualifies to be part of this investigation. However, we picked a diverse collection of apps to provide proof that such a suspicious practice of snooping on the pasteboard exists in many apps.
There is a considerable number of apps that only read the content of the pasteboard on launch. That is, the app reads the pasteboard only when it is opened for the first time. The next time it reads the pasteboard again is when the app is quit and relaunched. Although such a behavior is also suspicious, we decided to exclude such apps and focus on the ones that access the pasteboard more frequently.
As noted in our previous article, an app that accesses the pasteboard can also read what has been copied on a Mac if Universal Clipboard is enabled.
Findings#
While unrestricted access to the pasteboard allow apps to read any data type, all the apps we investigated for this article have only requested access to text data. In other words, they are only interested in reading text and ignore other data types that may have been copied to the pasteboard, such as photos and PDF documents. Surprisingly, none of the widgets that were tested accessed the pasteboard.
Our findings only documented apps that read the pasteboard every time the app is opened. However, apps can delay snooping on the pasteboard until some time or event takes places (e.g. signing up), hence are not included in our findings.
List of Apps#
This section summarizes the list of apps that snoop on the pasteboard every time the app is opened. The apps are listed alphabetically in the following format:
- App Name — BundleID
UPDATE (AUGUST 16, 2020): More apps crossed out *
UPDATE (JUNE 30, 2020): The list of apps in the original report from March 2020 is NOT an exhaustive list. We examined a sample of popular apps, and listed the ones that exhibited the behavior of excessive clipboard access. Many apps have been updated since then. In light of that, we tested the apps again. The apps that stopped reading the clipboard are crossed out.
We thank developers who updated their apps to fix this privacy issue.
News#
ABC News com.abcnews.ABCNewsAl Jazeera English — ajenglishiphoneCBC News — ca.cbc.CBCNewsCBS News — com.H443NM7F8H.CBSNewsCNBC — com.nbcuni.cnbc.cnbcrtipad*Fox News — com.foxnews.foxnews*News Break — com.particlenews.newsbreak*New York Times — com.nytimes.NYTimes*- NPR — org.npr.nprnews
ntv Nachrichten — de.n-tv.n-tvmobil- Reuters — com.thomsonreuters.Reuters
Russia Today — com.rt.RTNewsEnglish*- Stern Nachrichten — de.grunerundjahr.sternneu
The Economist — com.economist.lamarr*The Huffington Post — com.huffingtonpost.HuffingtonPost*The Wall Street Journal — com.dowjones.WSJ.ipad*Vice News — com.vice.news.VICE-News*
Games#
8 Ball Pool™ — com.miniclip .8ballpoolmultAMAZE!!! — com.amaze.game- Bejeweled — com.ea.ios.bejeweledskies
- Block Puzzle — Game.BlockPuzzle
Classic Bejeweled — com.popcap.ios.Bej3Classic Bejeweled HD — com.popcap.ios.Bej3HD- FlipTheGun — com.playgendary.flipgun
Fruit Ninja — com.halfbrick.FruitNinjaLite*- Golfmasters — com.playgendary.sportmasterstwo
Letter Soup — com.candywriter.apollo7- Love Nikki — com.elex.nikki
- My Emma — com.crazylabs.myemma
- Plants vs. Zombies™ Heroes — com.ea.ios.pvzheroes
- Pooking - Billiards City — com.pool.club.billiards.city
PUBG Mobile — com.tencent.igTomb of the Mask — com.happymagenta.fromcoreTomb of the Mask: Color — com.happymagenta.totm2- Total Party Kill — com.adventureislands.totalpartykill
- Watermarbling — com.hydro.dipping
Social Networking#
TikTok — com.zhiliaoapp.musically- ToTalk — totalk.gofeiyu.com
- Tok — com.SimpleDate.Tok
Truecaller — com.truesoftware.TrueCallerOtherViber — com.viberWeibo — com.sina.weibo*- Zoosk — com.zoosk.Zoosk
Other#
10% Happier: Meditation — com.changecollective.tenpercenthappier5-0 Radio Police Scanner — com.smartestapple.50radiofreeAccuweather — com.yourcompany.TestWithCustomTabs*AliExpress Shopping App — com.alibaba.iAliexpress*Bed Bath & Beyond — com.digby.bedbathbeyond*Dazn — com.dazn.theAppHotels.com — com.hotels.HotelsNearMeHotel Tonight — com.hoteltonight.prod- Overstock — com.overstock.app
Pigment - Adult Coloring Book — com.pixite.pigment*Recolor Coloring Book to Color — com.sumoing.ReColorSky Ticket — de.sky.skyonline*The Weather Network — com.theweathernetwork.weathereyeiphone*
Conclusion#
Access to the pasteboard in iOS and iPadOS requires no app permission as of iOS 13.3. While the pasteboard provides the ease of sharing data between various apps, it poses a risk of exposing private and personal data to suspicious apps. We have investigated many popular apps in the App Store and found that they frequently access the pasteboard without the user being aware. Our investigation confirms that many popular apps read the text content of the pasteboard. However, it is not clear what the apps do with the data. To prevent apps from exploiting the pasteboard, Apple must act.
Media Coverage#
This article was well-received in social media and has been covered by several tech websites. The following list provides links to the coverage:
- https://www.theverge.com/2020/7/4/21313214/reddit-code-clipboard-privacy-copy-ios
- https://www.telegraph.co.uk/technology/2020/06/25/tiktok-stop-snooping-users-clipboards-iphone-update-shows-app/
- https://www.telegraph.co.uk/technology/2020/03/30/popular-apps-can-read-phones-clipboard-without-permission/
- https://www.bbc.com/news/technology-53305388
- https://arstechnica.com/gadgets/2020/06/tiktok-and-53-other-ios-apps-still-snoop-your-sensitive-clipboard-data/
- https://www.bbc.com/news/uk-53223463
- https://nakedsecurity.sophos.com/2020/06/30/ios-14-flags-tiktok-53-other-apps-spying-on-iphone-clipboards/
- https://www.independent.co.uk/life-style/gadgets-and-tech/news/iphone-clipboard-data-tiktok-ios-14-a9603461.html
- https://www.imore.com/what-clipboard-snooping-and-should-i-be-worried-about-it
- https://www.gizmodo.com.au/2020/07/ios-clipboard-apps-spy-tiktok/
- https://www.forbes.com/sites/zakdoffman/2020/03/12/simple-apple-security-hack-if-you-have-tiktok-on-your-iphone-look-away-now/
- https://www.idropnews.com/news/be-careful-what-you-copy-these-apps-are-scanning-your-iphones-clipboard
- https://www.imore.com/apps-including-tiktok-can-read-your-ios-clipboard-without-permission
- https://www.iphone-ticker.de/ios-zwischenablage-zu-gespraechig-benoetigt-ios-14-neue-abfragen-154833/
- https://www.macrumors.com/2020/03/15/ios-apps-pasteboard-data-report/
- https://mashable.com/article/iphone-clipboard-spying-tiktok
- https://www.zdnet.com/article/these-popular-iphone-and-ipad-apps-are-snooping-on-data-copied-to-the-clipboard/
- https://appleinsider.com/articles/20/03/13/popular-apps-like-tiktok-are-snooping-on-your-iphone-clipboard
- https://www.consumeraffairs.com/news/many-popular-apple-app-store-apps-spy-on-users-pasteboard-data-031620.html